Let’s Encrypt: A Free SSL Certificate For Everyone
The days of unsecured websites are coming to an end. Many tech giants are stepping up the war against un-encrypted websites. Just this month Google announced that Chrome browser will start flagging websites that do not use encryption as “Not Secure”. Normally to enable encryption on your website, you need to get and install a certificate from a Certificate Authority (CA). The certificate can be bought for a yearly charge and requires some fiddling with your Webserver in order to install it. Things are now different with Let’s Encrypt.
Let’s Encrypt
Let’s Encrypt is a free, automated, and open certificate authority (CA), run for the public’s benefit.
This certificate authority is supported by many tech giants companies such as Mozzila, Cisco, Google, Facebook and others.
I have decided to benefit from Let’s Encrypt and encrypt the Lazy Engineers blog. Using Let’s Encrypt, Certbot and Google Compute Engine I was able to do it under 15 minutes.
Note:
You need to have shell access (ssh) to your server in order to do this. Also you need to understand basic Linux commands. But it is pretty much straight forward.
Install Certbot
Certbot is an automated tool to get and install the certification on your server.
The installation steps will differ depending on your server configuration. To get the required steps for your own environment you can visit Certbot home page and choose the corresponding settings.
For my environment I am running Apache on Debian 8 server. So after connecting through SSH to my server I executed the following commands.
|
1 |
sudo apt-get install python-certbot-apache -t jessie-backports |
Run Certbot Script
Certbot has an Apache plugin builtin. So all you need to do is run the below command and follow the onscreen steps.
|
1 |
sudo certbot --apache |
- The first time you run it, it is not going to find any existing configuration files. Just hit yes on the first screen to proceed to the next on.
- On the second screen you will be asked to enter the domain name for your website. In my case www.lazyengineers.com.
- Now you have to enter the contact email address. As it shows in the photo below, the email will be used for notices and lost key recovery.
- The usual Terms of Services screen. “Read” and agree to the terms of services.
- On the last configuration screen, choose if you want to allow unencrypted access to our website or limit it to encrypted connections only.
The bot has created a certificate for the website using Let’s Encrypt CA. It has also installed the certificate inside Apache webserver.
You can visit SSL Labs and check the status of the website security.
|
1 |
https://www.ssllabs.com/ssltest/analyze.html?d=www.lazyengineers.com&latest |
Replace www.lazyengineers.com with your own domain.
Let’s Encrypt Expiration
The Let’s Encrypt certificate is valid for 90 days. After 90 days you will need to renew the certificate or it won’t be valid anymore.
This process can be automated using certbot and systemd.
First run the below command to simulate a renewal process and make sure that everything runs smoothly without any errors.
|
1 |
sudo certbot renew --dry-run |
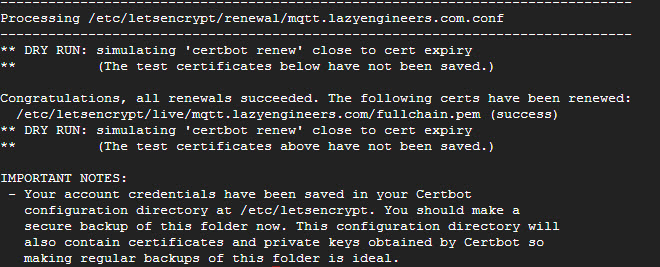
If everything went as expected we can proceed to automate the above process using systemd
Using a text editor, we need to create a systemd service. We will call the service “certbot.service”
|
1 |
sudo nano /etc/systemd/system/certbot.service |
Paste the below inside the text, save and exit.
|
1 2 3 4 5 6 |
[Unit] Description=Let's Encrypt renewal [Service] Type=oneshot ExecStart=/usr/bin/certbot renew --pre-hook "service /etc/init.d/apache2 stop" --post-hook "service /etc/init.d/apache2 start" --quiet --agree-tos |
The above service stops the Apache2 server, it runs the renewal command and then starts the Apache2 server again.
Give it a quick test using
|
1 2 |
sudo systemctl start certbot.service sudo systemctl status certbot.service |
If you do not see any errors after running the status command, you are ready to schedule a timer.If you get errors you will need to look into the service we created in the previous step.
Using a text editor, we need to create a systemd timer. The timer will run the script everyday at 2:00 AM to check and renew the certificate. Let’s Encrypt recommends adding a random delay to the script so that their server won’t be overloaded.
To create the timer
|
1 |
sudo nano /etc/systemd/system/certbot.timer |
Paste the below inside the text, save and exit.
|
1 2 3 4 5 6 7 8 9 10 |
[Unit] Description=Daily renewal of Let's Encrypt's certificates [Timer] OnCalendar=*-*-* 02:00:00 RandomizedDelaySec=3600 Persistent=true [Install] WantedBy=timers.target |
The final step is to enable and run the timer inside systemd
|
1 2 3 |
sudo systemctl daemon-reload sudo systemctl enable certbot.timer sudo systemctl start certbot.timer |
That is it, everything is now done and automated. No more user actions are required.
Latest posts by Hisham Daou (see all)
- Reimagine Lebanon… Win 10,000 USD - December 28, 2016
- Lazy Chip Search: Free Chrome Extension - November 21, 2016
- Arduino: The Beginning Of The End ?! - October 28, 2016